Securing Public Cloud Applications with Valtix
Valtix provides network security-as-a-service for protecting applications hosted in public Clouds. Valtix enables customers to discover their applications in public Cloud, deploy Valtix Gateways to inspect traffic, and defend with dynamic security policies that protect Internet-facing applications from attacks, prevent exfiltration and stop lateral movement of threats.
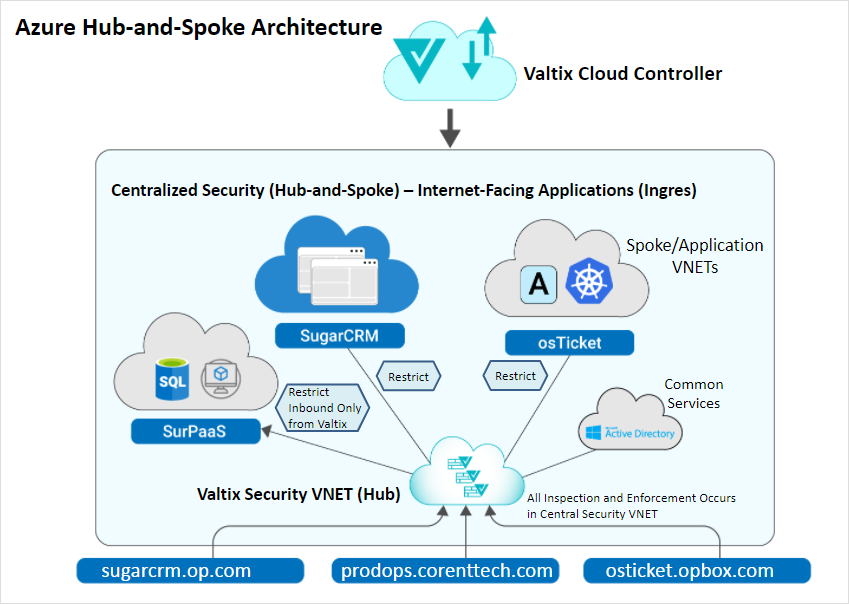
Corent used Valtix to manage and govern security across multiple deployments in Microsoft Azure from a single web portal.
Requirements:
Three applications in Microsoft Azure need to be secured and each deployment was in a different Azure subscription.
All the deployments are Internet-facing and accessed via different URLs.
Providing advanced network security for the three deployments through a single security deployment.
Ensure a fast and simple deployment of security without changing the application or requiring extensive expertise in Cloud networking and security.
Solutions:
Valtix SaaS to quickly discover all workloads across multiple Azure subscriptions.
Deployed Valtix Gateways inside Azure subscription of Corent with a hub-n-spoke architecture.
Setup security policies to protect Internet-facing traffic with WAF and IDS/IPS policies. Setup egress filtering policies with TLS decryption and URL filtering.
Result:
Corent was able to run a proof of concept within hours and after a week of testing, enabled an advanced network security solution to protect against attacks and prevent exfiltration, enabling them to meet the compliance needs of the customer.