When compared to standard enterprise datacenter migration, working with federal and public sector organizations requires further considerations to be made. Working with such clients only increases the number of requirements you have to worry about, whether it is around compliance and security, or verification and clearance; it’s just how this industry works. These organizations, when performing their migration, want the process to be as secure as possible, eliminating any chances of data breaches or any other technical calamities, and providing the additional care required to manage any IT process within these organizations. There are only three primary criteria in this market: Security, Security, and Security. To operate in this space, service providers must understand the many nuances of these criteria and address it accordingly, handling most of the concerns in federal and public sector IT space. One company that has effectively managed these concerns is General Dynamics IT (GDIT), a very respected IT services company with vast experience in Cloud transformation, serving Federal and Public sector industry in Defense, Health, Federal Civilian, Intelligence Community, State, and National Security. As such, we, at Corent, are immensely proud to have a partner like GDIT to help us create and offer a joint solution for Cloud Migration in this space.
Tool requirements in Federal and Public sector space
Before choosing a software tool for your datacenter assessment, it is crucial to assess the specifications it needs to meet. While many providers offer tools to address the Cloud Journey for advanced PaaS and Kubernetes services on the Cloud, the real challenge is to find a tool that fulfills the various, stringent requirements of these marketplaces. For instance, software tools must be compliant to one or more of the specific security requirements established by the Federal organization, without which the tools are neither secure nor appropriate for your usage. Any further certifications and criteria that a tool meets, like the FedRAMP certification and ISO criteria, can add tremendous value, providing you with an additional layer of authenticity and safety. However, the main criteria are how the tools are deployed at federal datacenters, for assessment and migration, as well as the method of scanning and assessment you utilize, both of which have a significant impact when it comes to addressing security and efficiency concerns. With our new, joint solution with GDIT, we aim to effectively address these requirement concerns, simplifying your entire Cloud journey, from assessment to migration.
3 Deployment models
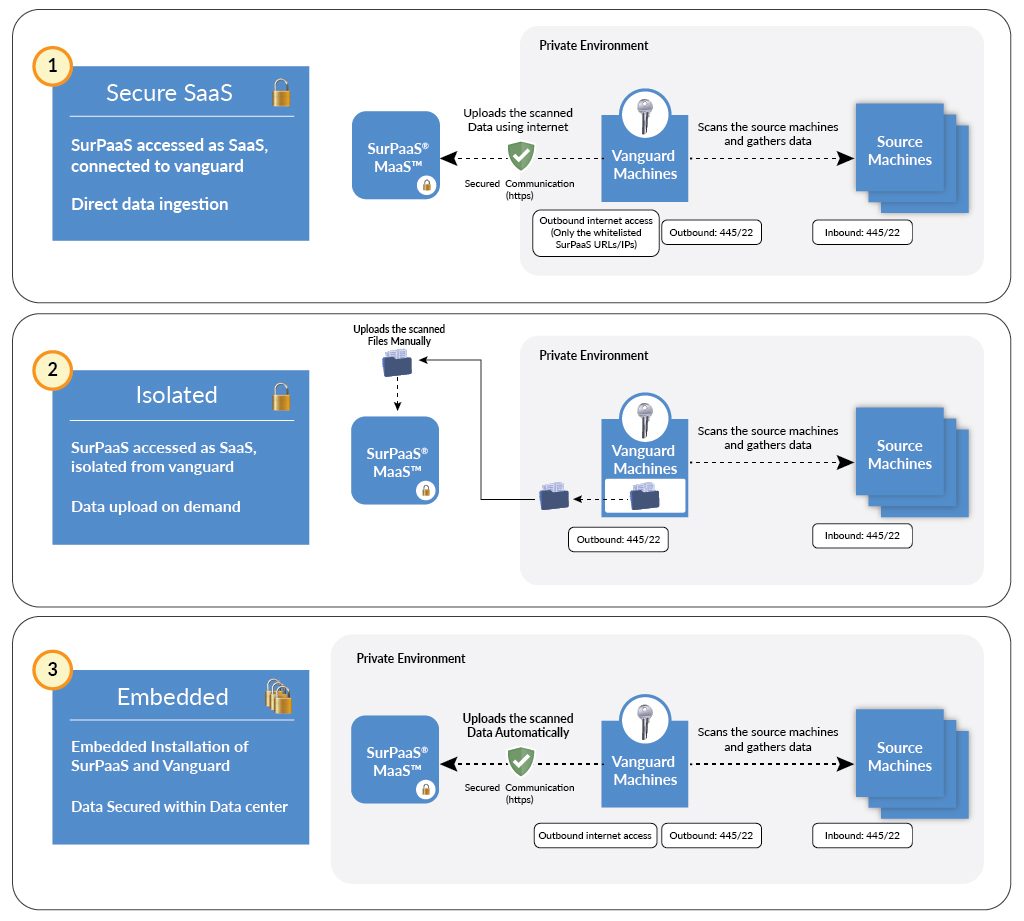
The strategy with which you choose to deploy your scan and assessment tool is a vital one, as the chosen method must adhere to the requirements. With this in mind, here are three models that Corent offers to deploy tools into federal and public datacenters:
- Secure SaaS Model– Your IT infrastructure team reviews the prerequisites and security requirements, running, in some cases, a Vanguard or bastion server inside the network that captures data from the datacenter and sends it to a SaaS-based system for analysis. What is imperative here is to ensure that the data collected is indeed the metadata of the infrastructure and software services, then encrypting that data at rest and in transit.
- Active in Isolation Model– A more secure strategy that ensures that the Vanguard server inside the network does not communicate with any external networks during the process of scanning, thereby easing any potential concerns. After the scan’s completion, this server can be isolated, and the collected information is ready to be sent to the system that analyzed the data.
- Embedded Tools Model– With this method, no security violation is left unchecked, as the entire toolchain is deployed inside the firewall. However, this is an expensive approach, since the tools to be deployed within the federal infrastructure must undergo stringent checks, ensuring that it cannot be a security threat before its use. Additionally, the tool provider must have the necessary support infrastructure in place to enable and maintain such a deployment model, thus limiting your options to a small group of providers.
5 Scan Methods to choose from
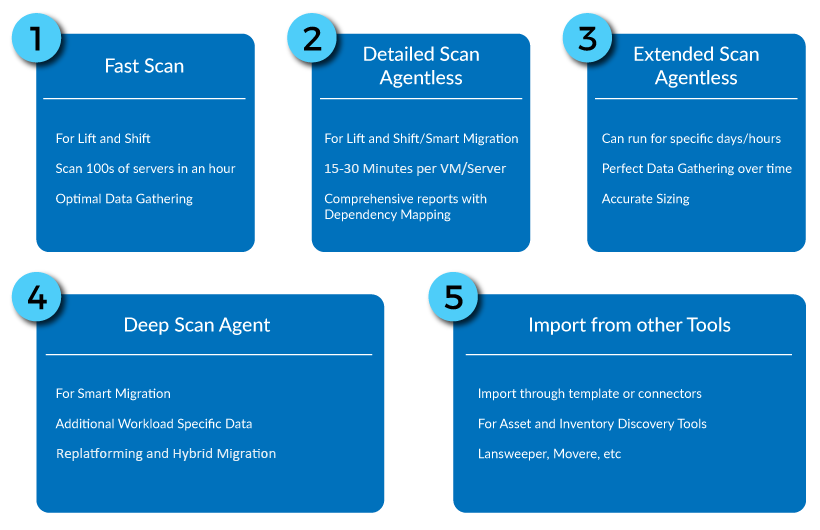
Similar to how there are multiple deployment models you can choose from, there are several techniques you can utilize to scan the IT infrastructure within a federal or public sector organization. Each method requires different security requirements and access permissions to communicate with each server, or VM, in the datacenter, enabling you to choose the approach that works the best for you. With that said, here are the five methods at your disposal:
- Fast Scan (Agentless)
- Quick and efficient
- Collects the information necessary to make immediate judgments on Lift and Shift operations to Cloud
- Includes the rightsizing of VMs, based on preliminary data
- Detailed Scan (Agentless)
- Generates more comprehensive information, to help you make well-informed decisions
- Gathers performance data for sizing the VMs, which are provisioned on the Cloud
- Extended Scan (Agentless):
- Captures performance data over longer periods, to analyze the trends of CPU and RAM performance/utilization and accurately model the target environment
- Useful for tracking additional services, like cron jobs, which may start at different times; a phenomenon that other methods might not catch.
- Deep Scan (with Agent)
- Surveys deeper into workloads to capture additional data, such as tables and procedures for databases, configurations of specific workloads, etc.
- Is more intrusive in its scans of servers, generally discouraged because of its effects on the production system
- More effective when making decisions on migrating to more advanced services, such as PaaS, Containers, Kubernetes, etc.
- Import from other tools
- Versatile; allowing data to be imported into analysis tools, from other IT asset management tools or performance monitoring tools, to create a migration plan
For more detailed information on these different scan methods, visit our previous discussion on the topic here: Click Here.
Migration after assessment
After the completion of the assessment, the servers and VMs must be migrated to the Cloud; this requires migration tools to be readily accessible to initiate migration. However, before you start utilizing the tools, you must choose how you want to handle the migration of your assets, as migration can be of various, unique types. The following are but a few ways you can proceed with migration:
- Lift and Shift – With this procedure, the source server or VM, from the federal or public sector datacenter, is packaged and moved to the Cloud to populate an equally sized VM, along with its OS; which remains the same.
- Replatform – The right version of the OS may not always be available on the Cloud. This method works best under these circumstances, as software workload needs to be installed on the Cloud, on a different version of the OS. Sometimes, the version of the workload needs to be updated so that the process of migration could remain the same; which this method handles perfectly.
- Retopologizing – A software consists of multiple workload components. By Retopologizing, it is possible to split these different workloads and install them on separate VMs on the Cloud, to make the entire application scalable.
- PaaS migration – When using this method, you move beyond Infrastructure as a Service (IaaS) and explore Platform services (PaaS) to move workload, so that redundancy is avoided and cost efficiency is maintained.
- Serverless migration – This method pushes the application into serverless code running on App Service, thus eliminating the need to bring up your VMs and manage them along with the application server; this saves you time on the actual migration, allowing you to focus on other aspects of the Cloud Journey.
- Move to Containers – By utilizing this method, you can leverage the subcomponents of the application and package them into containers. This allows you to install all the components on a single VM or on multiple containers in a smaller number of VMs.
- Move to Kubernetes services – This method leverages the platform offered by Cloud providers to manage container workloads and to scale.
Value of an Integrated platform
Now that you have chosen a migration approach, it is now time to incorporate your preferred tool into the datacenter of your choice. However, before beginning the actual process of migration, it is vital that you recognize that every time a new tool is introduced into a federal or public sector organization’s datacenter, it has to be qualified and cleared for use. Since, generally, multiple tools need to be employed to perform scanning, analysis, and one for each type of migration, it would significantly reduce the required time to migrate if there was a single platform that handled all aspects of migration.
With this in mind, our incredible team of engineers have created a revolutionary product that offers you these benefits by aggregating all aspects of migration into one, easy-to-use platform. Here are some of the operations Corent can perform using its various integrated tool features:
- 5 unique methods of scanning.
- Assessment for Lift and Shift, as well as advanced forms of migration.
- Cost modeling and Total Cost of Ownership (TCO) analysis.
- Migration strategy planning.
- Integrated migration for Lift and Shift, Replatforming, Retopologizing, PaaS migration, Serverless migration, move to containers, and move to Kubernetes services.
- Post-migration synchronization up till switchover.
Service provider familiarity of tools and processes
Our friends at GDIT are well-versed with our platform, with team members fully equipped to handle scanning, assessment, and migration activities across various environments. The multiple deployment methods recommended in this discussion have been proven, by multiple federal and public sector organizations, to be secure and qualified for datacenter assessment and migration. For more information on these qualifications, please send a request to [email protected].
To close off this discussion, we introduce Neil Kronimus, from GDIT, who, in a recent webinar jointly hosted by AWS, Corent, and GDIT, presented on the challenges of Cloud migration and modernization, and how to address them from the perspective of a service provider with hands-on experience executing multiple projects in this space.

